Blog
Posts about
cybersecurity
What Your District’s Network Activity Is Telling You (and What to Do About It)
Every K-12 school district generates a heavy stream of digital activity—logins, file transfers, remote connections, e-mail monitoring, web browser ...
Smart Cybersecurity Budget Planning for K-12 Schools: Protecting Student Data in 2025
Budget Season is Here—Is Your District Investing Where It Matters? Cyberattacks on K-12 schools aren’t slowing down. In fact, the education sector ...
PowerSchool Breach Exposes SIS Vulnerabilities: How to Protect Your K-12 School District
Student Information Systems (SIS) are used by all K-12 schools and contain personal and academic data on students and staff. Unfortunately, this ...
The K-12 IT Leadership Roundtable Series
Managing IT operations in a K-12 school district is a multifaceted endeavor that requires a nuanced approach to balance educational innovation with ...
Endpoint Detection & Response: The Limitations of EDR Threat Analysis
Endpoint Detection & Response (EDR) has become an increasingly popular tool for organizations looking to protect their data and networks from ...
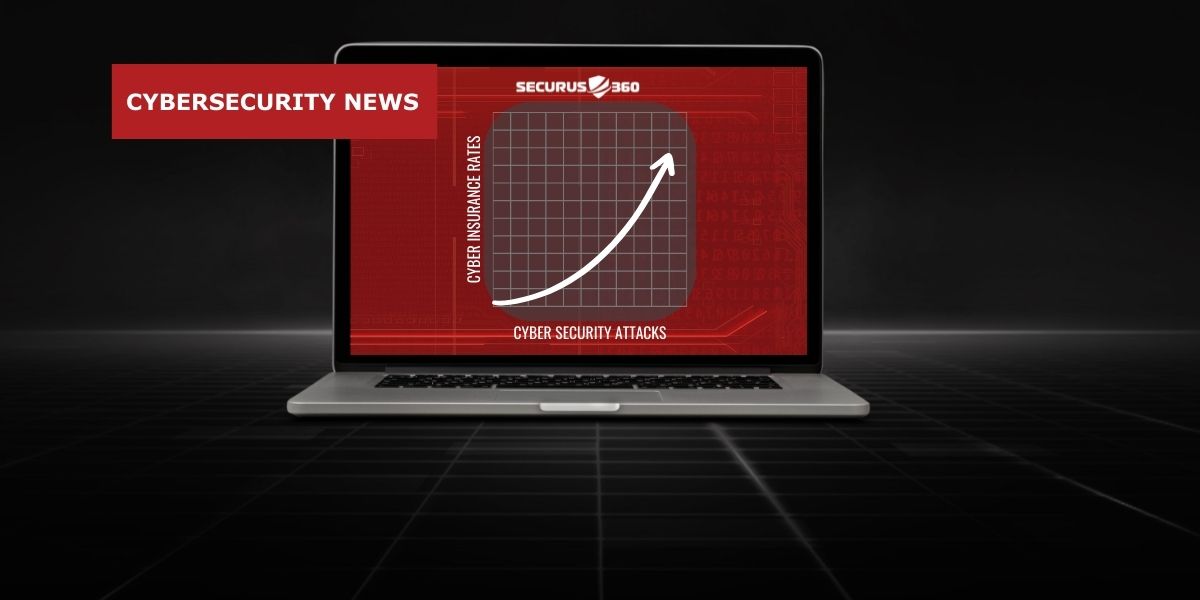
The Cyber Insurance Landscape is Undergoing a Seismic Shift - It's Not Good News
Rising cyber security attacks have made cyber insurance firms increase premiums and tighten policy language, while at the same time, reducing ...
Tips to Improve Your Organization's Cybersecurity Posture
A cyberattack can strike anywhere, any time. These threats are evolving at a rapid pace and companies are struggling to adapt to a more hostile ...
Top Cybersecurity Threats to the Education Sector
Ransomware Attacks Against K-12 & Secondary Education are Surging Ransomware attacks against K-12 education as well as colleges and universities ...
Rapidly Increasing Threats in the Education Sector – Why Cybersecurity Should be a Priority in 2022
Cybersecurity events in the education sector hit record highs in 2021 and are expected to continue to rise in 2022. These events are disruptive and ...
The Cybersecurity Risk of Ineffective Employee Offboarding
Employees, whether in office or remote, require onboarding when they join a company. This onboarding process is typically the first task accomplished ...