Protecting K-12 School Districts: Mitigating the Risk of a Data Breach
Data breaches have become a grave concern for organizations across various industries. K-12 school...
We monitor your entire infrastructure for threats
MXDR for Cloud Security ▼We see everything going on in your cloud instances
Next-Generation Cybersecurity for K-12 Education
MXDR for Office365 Security ▼Let us monitor Office365 for you
Platform for Cyber Analytic & Hybrid SecOps
Data Protection ▼Secure Your Data From Potential Threats
High Speed Cyber Defense to Thwart Threats in Real Time
Service Comparison ▼See How MXDR Compares to Other Platforms
Our experts weigh in on the cybersecurity landscape
What Superintendents Need to Know ▼Protect Your School District, Your Students, and Your Staff With Highly Specialized K-12 Cybersecurity
Our insights into complex cybersecurity challenges
Ransomware Calculator ▼How Much Could a Ransomware Attack Cost Your Business?
14 years of experience in Data Protection, Cybersecurity & Compliance.
Blind Spot ▼Short video on the problem we solve
Why are there still So Many Breaches? - As cyber breaches continue to evolve in sophistication, so do the technologies and tools designed to stop them. There has been a proliferation of cyber defense methods as the cybersecurity community races to keep the multi-billion-dollar cybercrime sector in check. Many organizations are investing heavily in security controls and approaches in an effort to protect themselves from the rising threats cyber criminals are deploying on a continual basis.
While an in-depth defense-in-depth strategy is regarded as an effective way to counter malware attacks and hacks, businesses continue to record data breaches almost daily. Most enterprises do not understand that deploying more cybersecurity technologies and tools does not mean it is the best way to prevent data breaches.
One speaker during the RSA conference 2019 attributed the proliferation of security tools within an organizational cybersecurity environment to the Lockheed Martin Cyber Kill Chain. The Kill Chain is a framework that assists organizations in detecting and preventing cyber breaches. It is a useful tool for enhancing a company’s cybersecurity posture, but the speaker noted that it gives security professionals a lot to manage. For example, the framework leads security personnel to deploy various tools in all parts of a Kill Chain and create discrete teams.
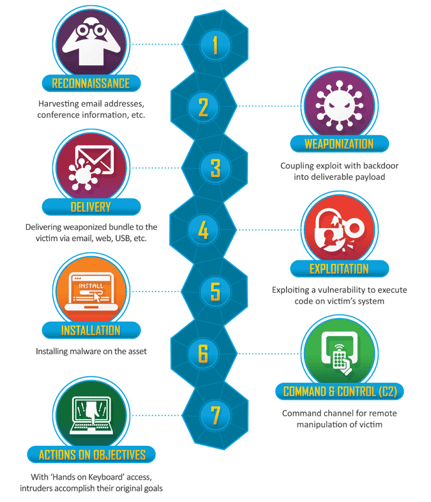
In addition to the Kill Chain, it is also essential to note that more robust cybersecurity procedures have necessitated organizations to invest in too many tools. The need for holistic cyber defenses is obvious, given the emergence of various data protection regulations and standards and the increased reliance on digital solutions for core business operations. Hiring cybersecurity experts seems like the best approach, but maintaining those individuals is too costly. Therefore, a company’s next best option is to complement the security professionals they CAN afford with a variety of tools.
Meanwhile, hardware and software solutions have emerged in a bid to fulfill the various cybersecurity needs of enterprises. Need a firewall to protect and filter your network traffic? There are software and hardware solutions for that. Need to log which users access which resources? There are a variety of tools that easily serve this purpose. In fact there are solutions that help address almost any cybersecurity issue, so many organizations have deployed a range of information security tools. This is where the challenge begins.
Organizations are slowly but surely enhancing the ability to detect and defend themselves from attacks. However, investing in numerous tools may reduce the effectiveness of the entire cybersecurity defense. IBM recently released the results of its fifth annual Cyber Resilient Organization Report, which featured a global survey done by the Ponemon Institute. The survey, which involved at least 3,400 IT and security staff, revealed that cybersecurity planning and investments are increasing, while effectiveness is declining. The survey showed that deploying many tools causes complexities due to the fragmented toolsets, which hinders the breach detection and response efforts.
In addition, the Cyber Resilient Organization Report found that enterprises have managed to enhance breach detection, response, and containment ability, but their capabilities to deter active threats has decreased by 13%. Businesses typically deploy 45 cybersecurity tools on average to protect their networks and systems. However, the widespread use of many technologies and tools minimizes the ability to detect breaches and reduces the ability to contain active attacks. The report found that businesses that deploy more than 50 cybersecurity tools register an 8% decline in threat detection effectiveness and a 7% decrease in defensive abilities, while companies using fewer tools and a team of experts have a more robust and effective cybersecurity posture.
Also, the more cybersecurity tools deployed, the higher the number of generated notifications and alerts. A useful cybersecurity tool must generate an alert in real-time upon detecting unusual network activities or system usage. However, most of the alerts tend to be false positives, meaning there isn't an actual threat. For example, an employee misusing company network resources may cause a spike in network traffic, in turn alerting an administrator of a potential threat. With many tools to manage, it may be overwhelming to view and manage all generated alerts. Moreover, most tools come with their own independent databases, which require monitoring.
According to another research study, enterprises that deploy many tools are required to manage at least 174,000 alerts and notifications every week. But due to the high number of false-positive alerts and notifications, some of these may be missed or ignored by cybersecurity analysts due to the overwhelming number of alerts they analyze daily. Also, they may lack time to address each notification since they must prioritize the most recent ones. Nevertheless, ignoring an attack deemed harmless may be an actual attack that results in a massive data breach.
Lastly, deploying too many tools forces an organization to deal with more vendors than necessary. It is not only challenging to keep up with multiple vendors, but it also requires a lot of hard work and dedication to foster and maintain the relationships. That said, companies may not have the time to track down the appropriate vendor in the event of a cybersecurity incident. Responding to a data breach in real-time is critical to containing the attack. Trying to identify the right vendor of the compromised tool takes away valuable time that can otherwise be used in responding to the incident.
All of the above examples boil down to one thing – investing in too many tools may actually leave you more exposed to cyber threats. But what is the solution? Protecting information and the systems supporting it requires an investment in the right cybersecurity tools to address and manage your threat environment, but this can be extremely expensive for a company to consider.
Securus360 enables enterprises to identify cybersecurity trends and the best countermeasures. Instead of spending too much on too many tools that can expose you to more attacks, you can complement your existing team and tool set with Securus360 Managed eXtended Detection & Response. Our MXDR platform is based on artificial intelligence and machine learning along with human cybersecurity analysts to ensure proactive, intelligent threat hunting, threat detection, and management.
Contact Us to Learn More!
Data breaches have become a grave concern for organizations across various industries. K-12 school...
Student Information Systems (SIS) are used by all K-12 schools and contain personal and academic...
Copyright © 2025 Securus360 | Privacy Policy | Cookie Policy | Terms and Conditions | Disclaimer